Sooner or later, Ransomware is likely to affect your business. Then what? Get the ITsMine Ransomware SOS guide with expert Guy Edri to learn from the experts what to do and when.
Guy Edri is an independent malware researcher, digital forensics & incident response examiner and ransomware expert.
Here, Guy provides specific steps, tips, and best practices when it comes to dealing with the aftermath of a ransomware attack.
What To Do After You Get Hit By Ransomware
What follows is a specific, proven step-by-step approach to get you and your organization back on your feet:
- Disconnect internet access
- Isolate the potentially infected machines
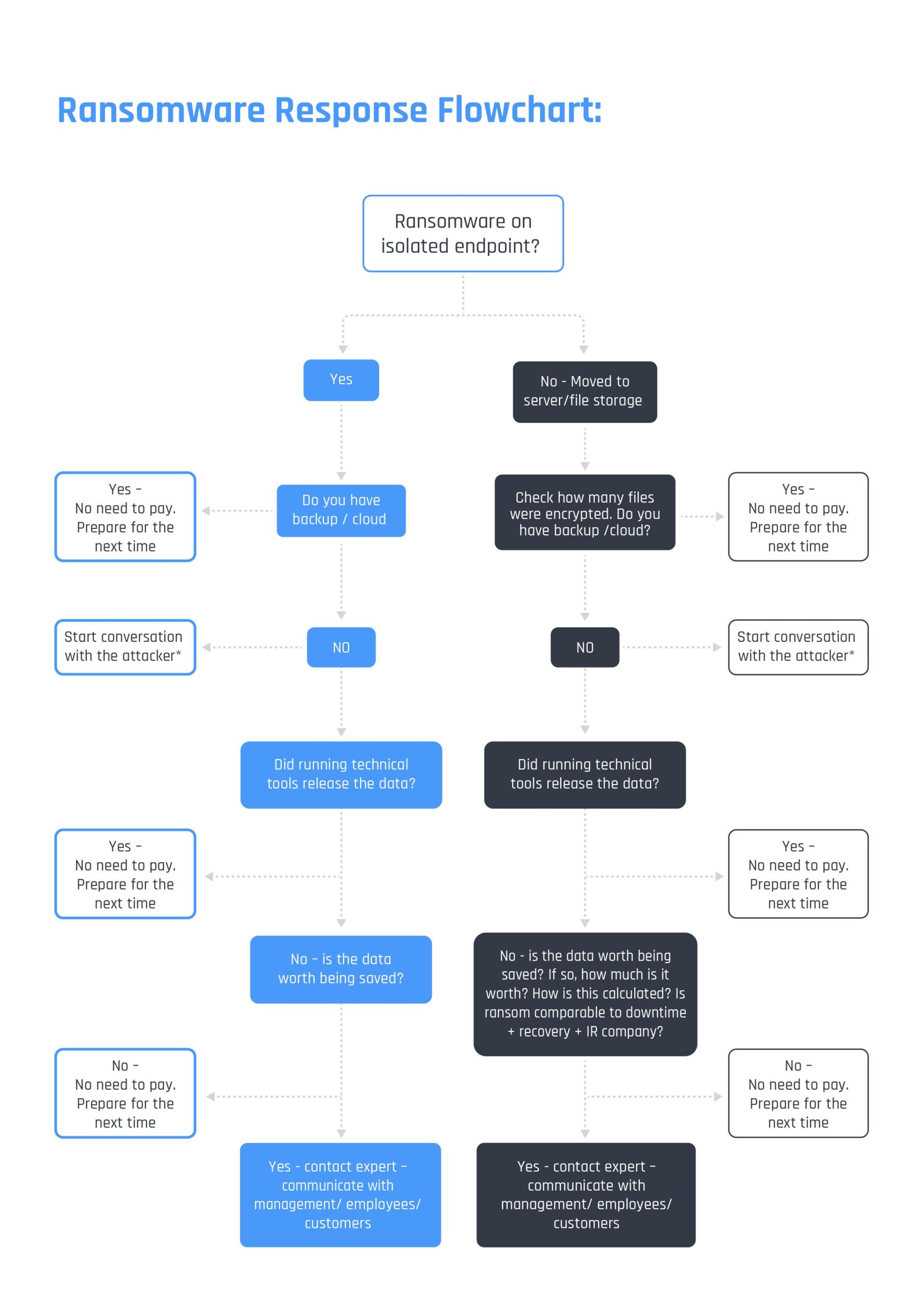
- Run the below flow chart – time is money, and you need to get the required data fast. If information is not available, assume the worst and move to the next level
- Check for backup (see that this too was not hit by the ransomware)
- How and where: Cloud, local, etc.
- Run tools like https://www.nomoreransom.org/
- In parallel to Step 1 start negotiations with the attacker. SEE ALL THE DETAILS IN “TIPS FROM A PROFESSIONAL NEGOTIATOR” BELOW (best practice is to hire a professional negotiator)
- It will not just “go away” – and you have a couple of hours before the cost will most likely double
- To pay or not to pay? Don’t make any decisions without consulting a professional
- Change your mindset: can you treat this as (expensive) penetration testing?
- Reinstall every device that had access to the infected device while the ransomware was active
- Plan how to recover the systems. If there wasn’t enough segregation in the network, now is the best time to remedy that going forward
- Call for IR (Incident Response) services to find the point of entry, and to close the holes that let the attacker get inside
After You Recover From The Attack, What Should You Do Next?
- Protect your managed devices – use tools like Microsoft Defender – and activate the ransomware protection on the devices (whitelist the processes that allow edits to the files).
- More information on this from Microsoft can be found here for Windows: https://support.microsoft.com/en-us/help/4013550/windows-protect-your-pc-from-ransomware
- And here for Mac: https://support.apple.com/en-il/guide/mac-help/mh40596/mac
- Upgrade the central logs of your security product (AV, EDR, etc) to the cloud
- Connect your cloud and file storages to get all access logs in order to easily investigate the changed/deleted/encrypted files from a location/user/PC etc. Keep the data for forensics for at least two years.
- Backup your files in the cloud/file storage – make sure you do not have leftover critical data on employee endpoints
- Plant SoftwareMines™ to make sure that your central file storages are protected from ransomware (even if the unmanaged device was infected)
- Educate employees to “close the door”. Revoke access automatically to areas they do not need access to anymore – as the ransomware uses the same access the users have
- Make sure all the systems have been patched to the latest security updates
- Harden all servers/workstations
- Subscribe to Threat Intelligence feeds
- Forward all logs from Servers, FW, AV, EDR/XDR, and other devices to a central log server like Splunk/ELK, etc. If there is enough of an InfoSec budget, consider a managed SOC service
- Have a proper incident response plan in place and a company on call that knows the entire infrastructure
- Perform a full Penetration Test/Gap Analysis once every 3-6 months
Tips From A Professional Negotiator
Cyber Crisis Negotiation: Do’s and Don’ts
Once you’ve been hit with a classic ransomware attack, with no backup or any technological remediation in sight – and the threat actor has initiated a “dialogue box”, be it as a link to a certain TOR window, confidential email account, or DM in social media – it is crucial to remember to following these ground-rules for effective negotiation:
- Dialogue is not an agreement to pay.
- Engage in a conversation to learn more about the threat actor
- Keep messages short. Ask simple questions and expect simple answers
- Hold your emotions. Angry and rude communication will lead you nowhere
- It’s “business”, nothing is personal – however, there are people communicating with you
- Don’t appeal to their logic, appeal to their emotions and human needs
- Never lie. If asked, consult your tech team for the best answer
- Expect no guarantees, but still ask for a “trouble-shooting” mechanism once you decide to pay
The 3 Cardinal Rules
There are three main rules to bear in mind after being hit by a ransomware attack:
- Don’t Panic
- Don’t Pay immediately
- Communicate openly with stakeholders
Don’t Panic:
This is what the attackers want you to do. At this sensitive time, almost as much damage can be done by doing the wrong thing, than by the attack itself. There are professionals out there who deal with these attacks all the time. Don’t panic, relax those shoulders, you’re going to get through this.
Don’t Pay Immediately:
The aim of the attackers of course is to extort money from you. Despite promises to the contrary, in many cases paying won’t mean that you get access to your data again. They will threaten, they will tease, but don’t be fooled into thinking that these people play fair.
Communicate openly with stakeholders:
Update people with what is happening. You don’t have to share all information, but it’s important to keep lines of communication open – including with stakeholders such as employees, customers, suppliers, regulators, and shareholders.
