No painful installations
Proactively prevent breaches
No classifications needed
Control your data everywhere
Empower employees
Easy regulatory compliance

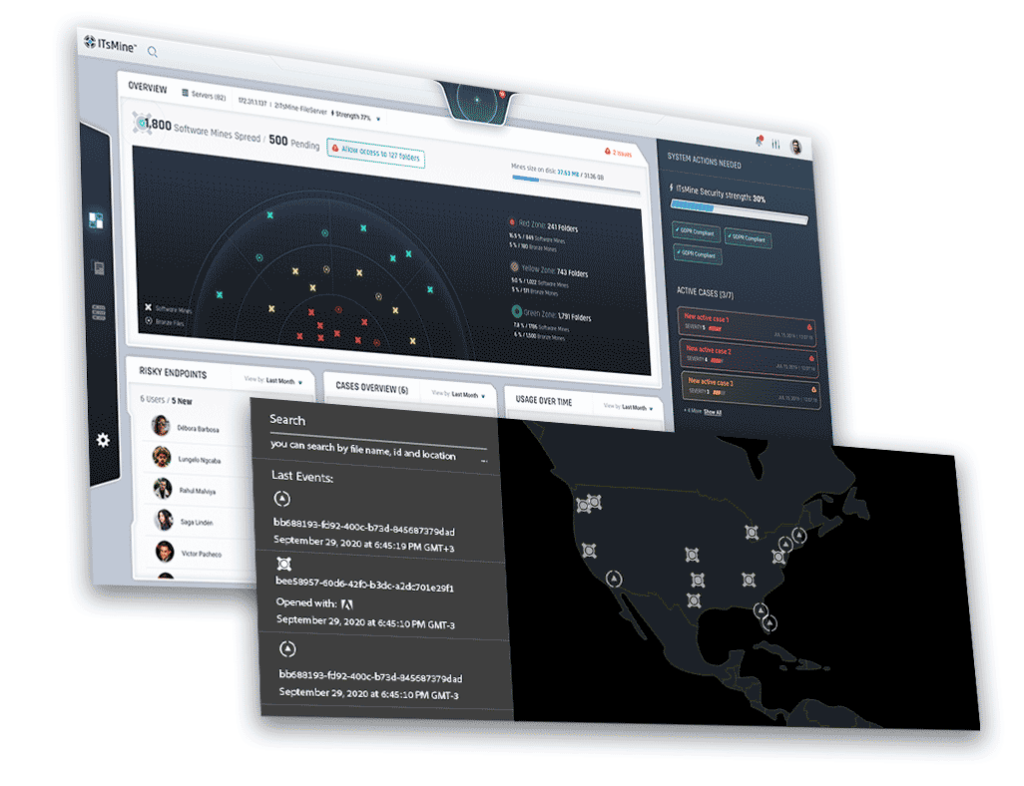
Track & control your scattered data’s location, anywhere: on-premise, in the cloud and on personal devices – by transforming any folder in your organization’s file storages into ‘Virtual Vaults’.
Key Features
ITsMine monitors and analyzes how users interact with organizational data to automatically detect and protect against a variety of threats, including data breaches, ransomware attacks, and careless or potentially malicious employee activity.
Key Features
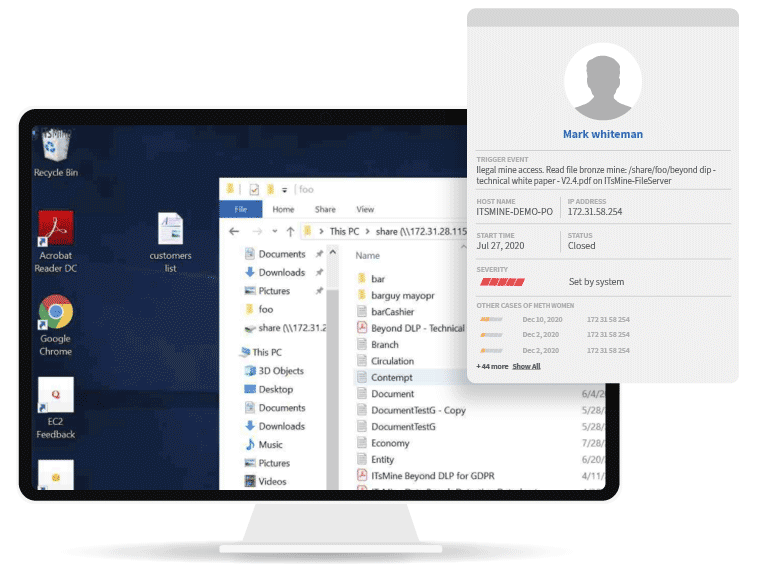
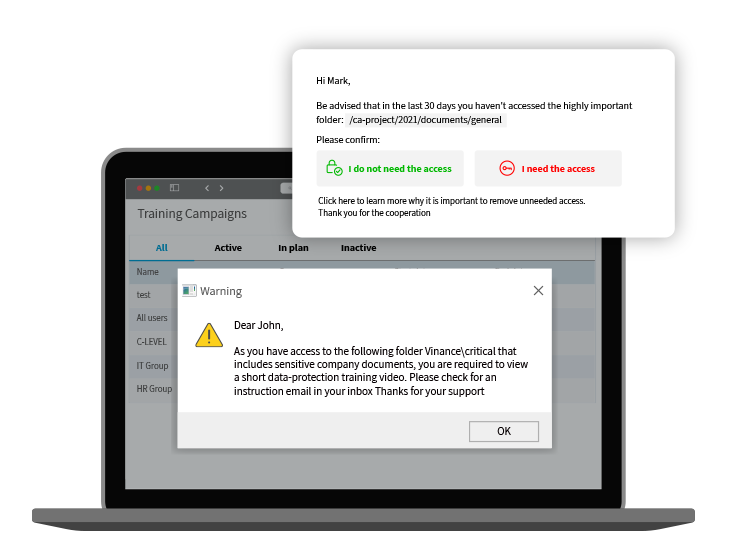
Engage employees in your organization’s data protection efforts by using integrated Data Security Awareness Training Campaigns and avoiding unnecessary access to data.
Key Features
Controlled sharing of sensitive data accessed by 3rd party entities – with options to monitor, time-limit and restrict data access if needed.
Maintain your high security standards regardless of whether your data is located in on-prem or cloud-based file systems.
Hassle-free compliance to data protection regulations, from GDPR, CCPA, PCI to HIPPA, with access control options to sensitive data, data breach detection and clear reporting options.
Empower employees’ full productivity while controlling usage and whereabouts of your sensitive data.
