Software tools
Expert instructions
Guides and resources
Preventative measures
Audit trails & evidence
Regulatory compliance
Experiencing a data breach or a potential data breach can be harrowing. We’ve gathered all the resources you need to guide you through the process of dealing with a breach – whether from a malicious outsider, a disgruntled insider or pure negligence.
Remember, you’re not the first one to experience a breach. It will be ok in the end, there is a light at the end of the tunnel. Choose from the resources below, and add ITsMine’s Emergency Deployment as soon as possible to begin damage control.

Including the first steps you need to take, from an expert in the field

What you need to know in terms of specific U.S State requirements

What you need to know in terms of specific EU requirements
By installing ITsMine now, you can actually “go back in time” and assess what happened, understand current situation and formulate your response.
You’ll need a product likeITsMine for evidence and audit trail purposes
You can choose to automatically deploy SoftwareMines™ in your file repositories to limit damage and protect data immediately.
Your stakeholders will want to know what actions you’ve taken: now you can demonstrate you’ve taken the initiative, and protected against further incidents
With SoftwareMines™ spread across the file server, suspicious behavior can be sensed immediately. When a SoftwareMine™ is set off – that is, exfiltrated and opened outside of the company’s environment – it will “call home” whenever and wherever it is used; thus providing an indication of a potentially significant data event.
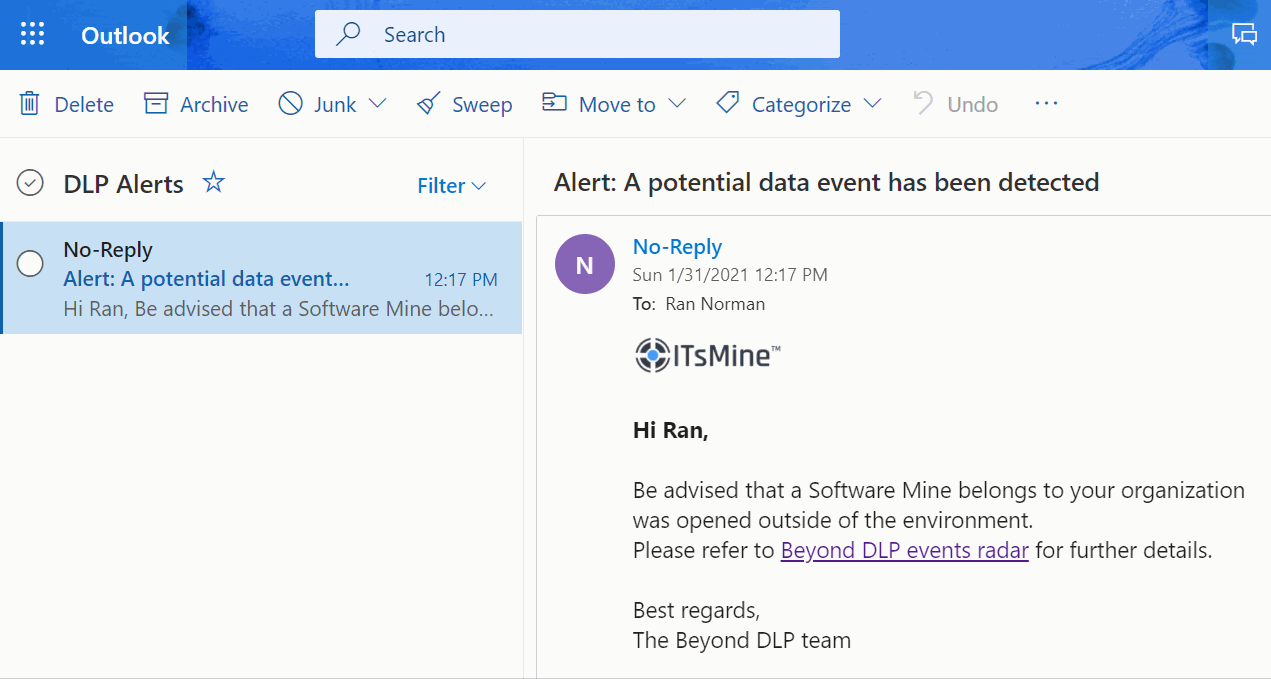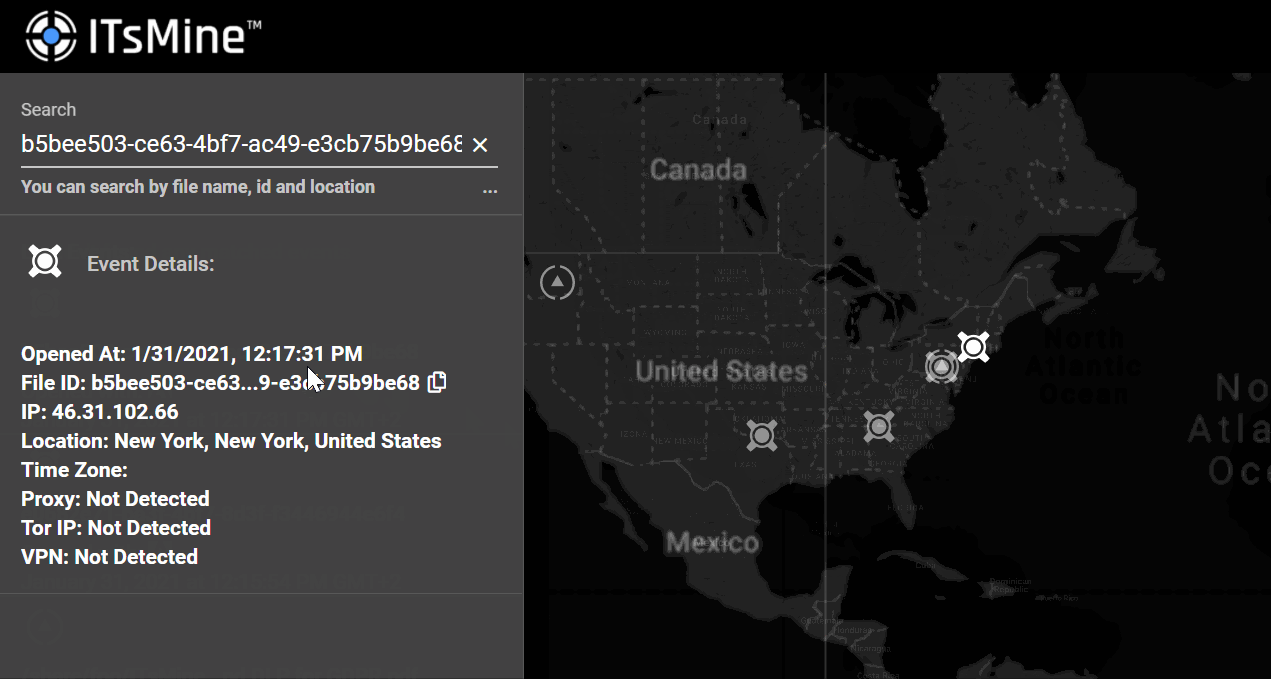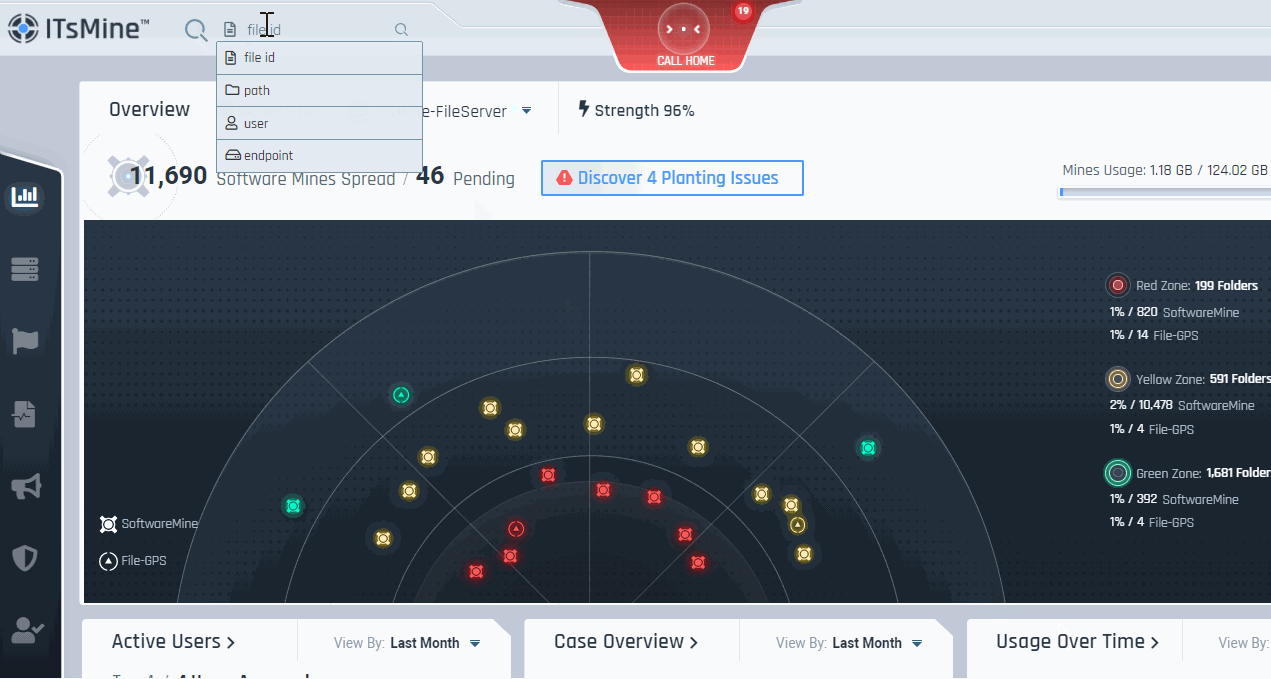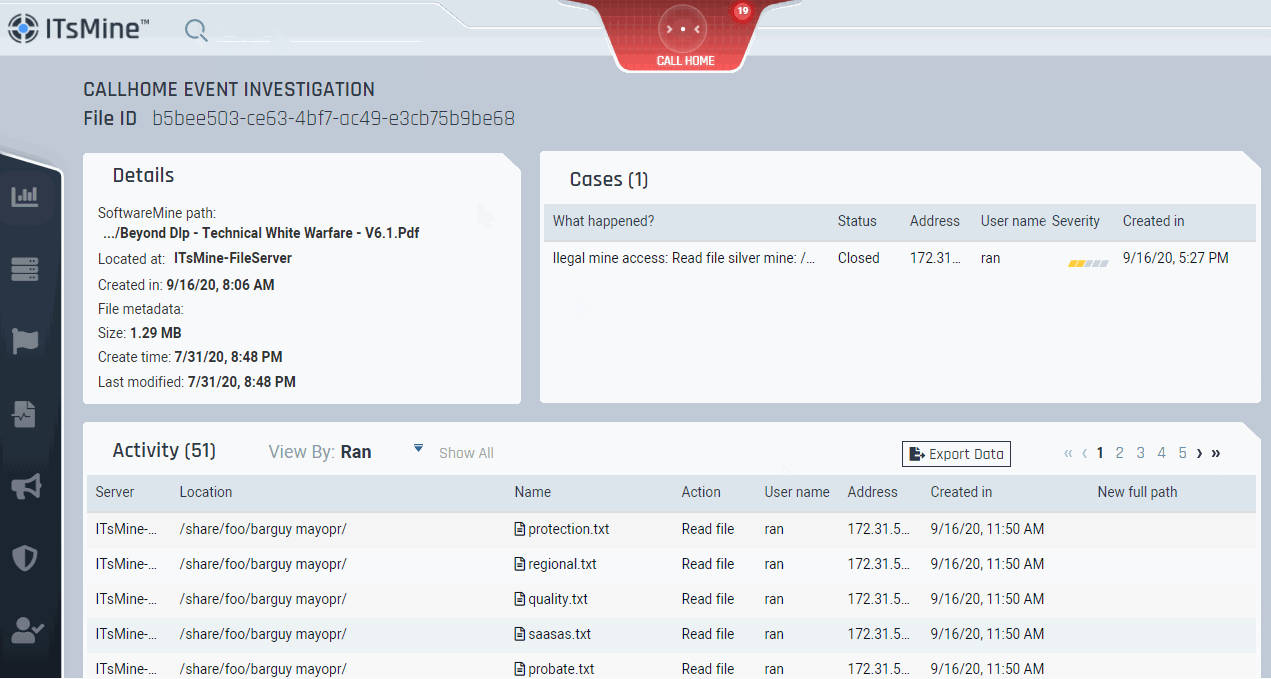
The unique identifier that is carried by the exfiltrated SoftwareMine™ will allow the company to get vital forensic information regarding this data event, including: when the event happened, who was responsible, and what other resources this entity took or accessed.
ITsMine’s unique method for protecting and centralizing files everywhere is by enabling you to create Virtual Vaults across any Microsoft, Google, Dropbox, or NetApp cloud solutions.
Files located in Virtual Vaults™ will automatically benefit from multiple layers of protection that will allow you to:
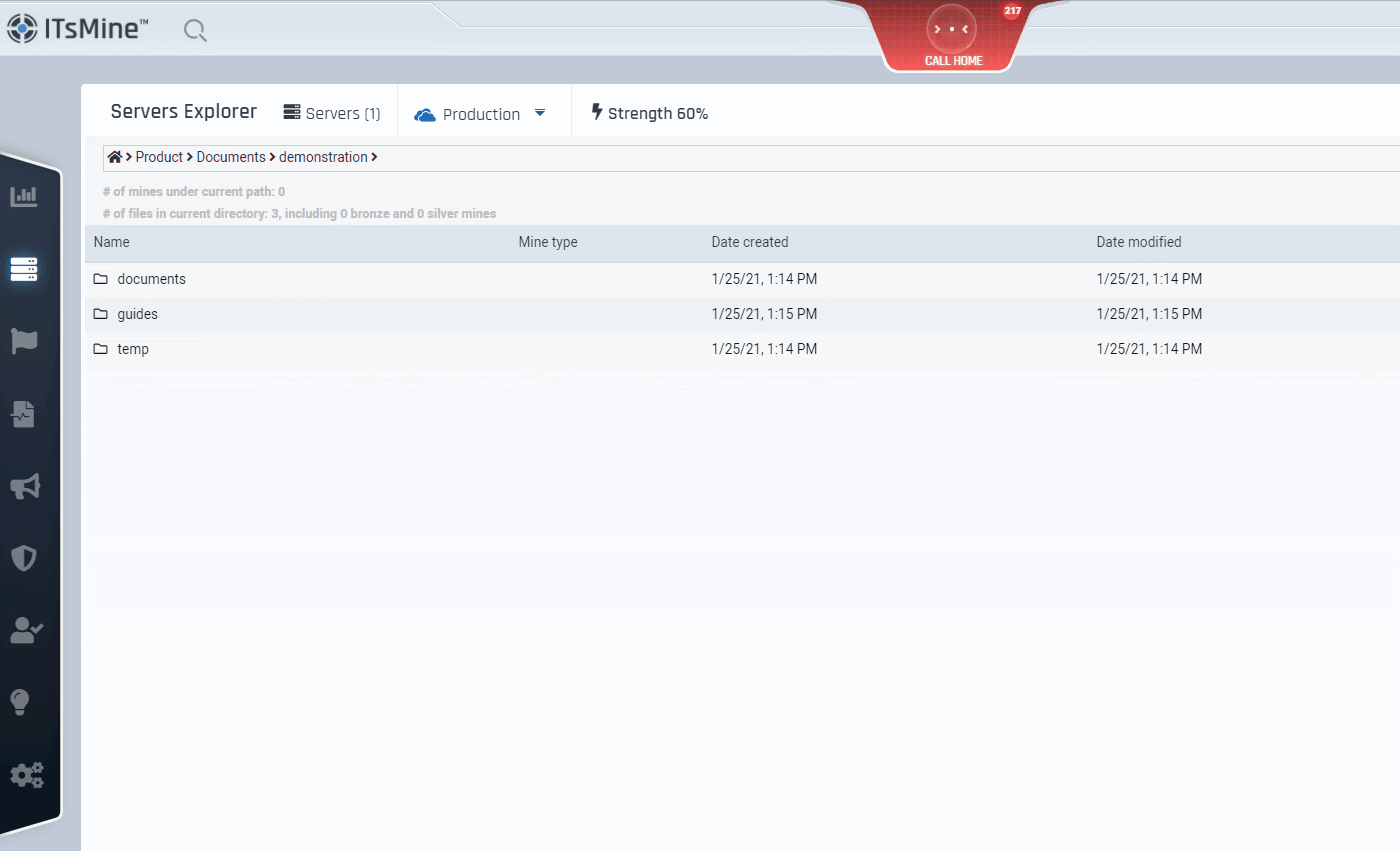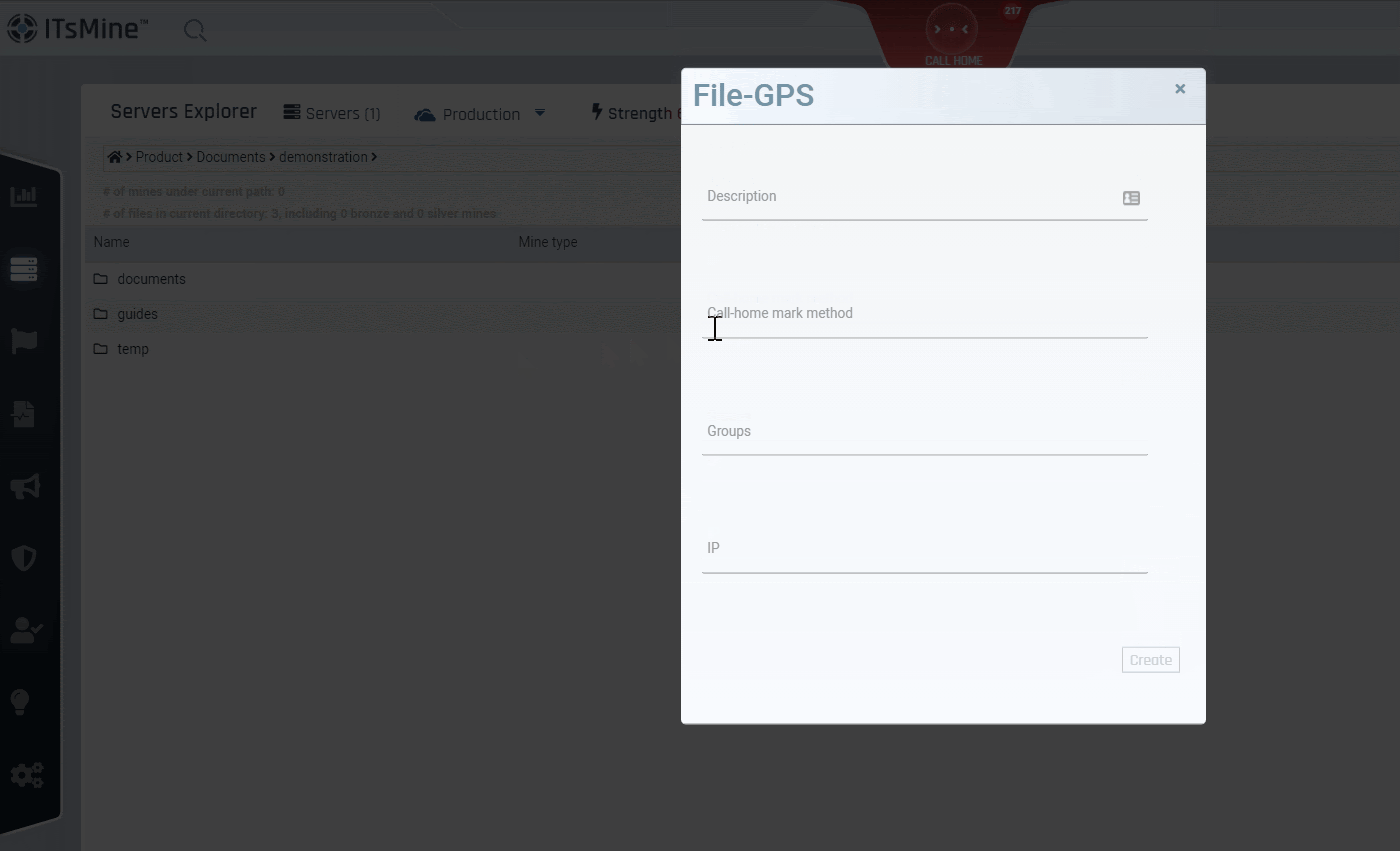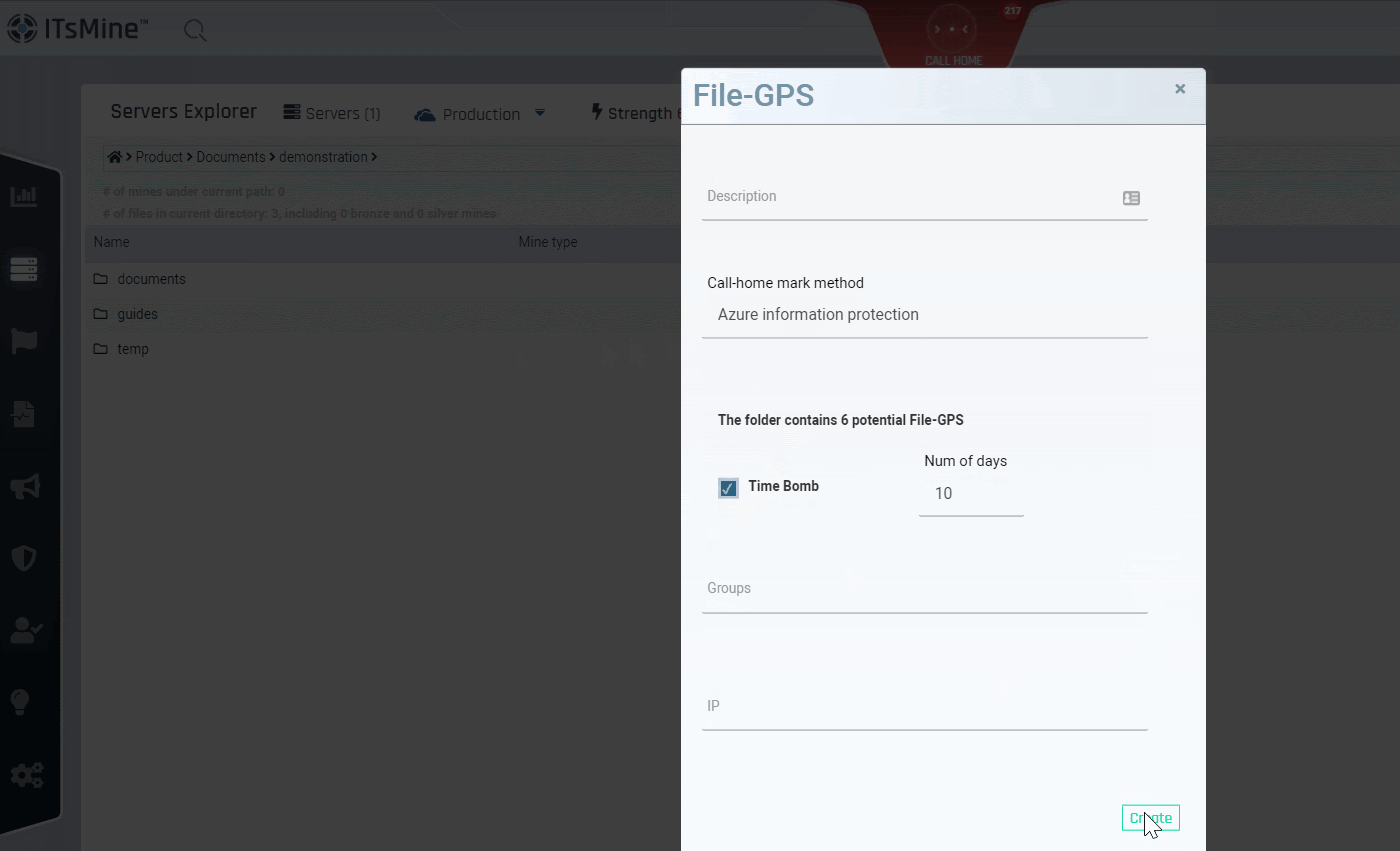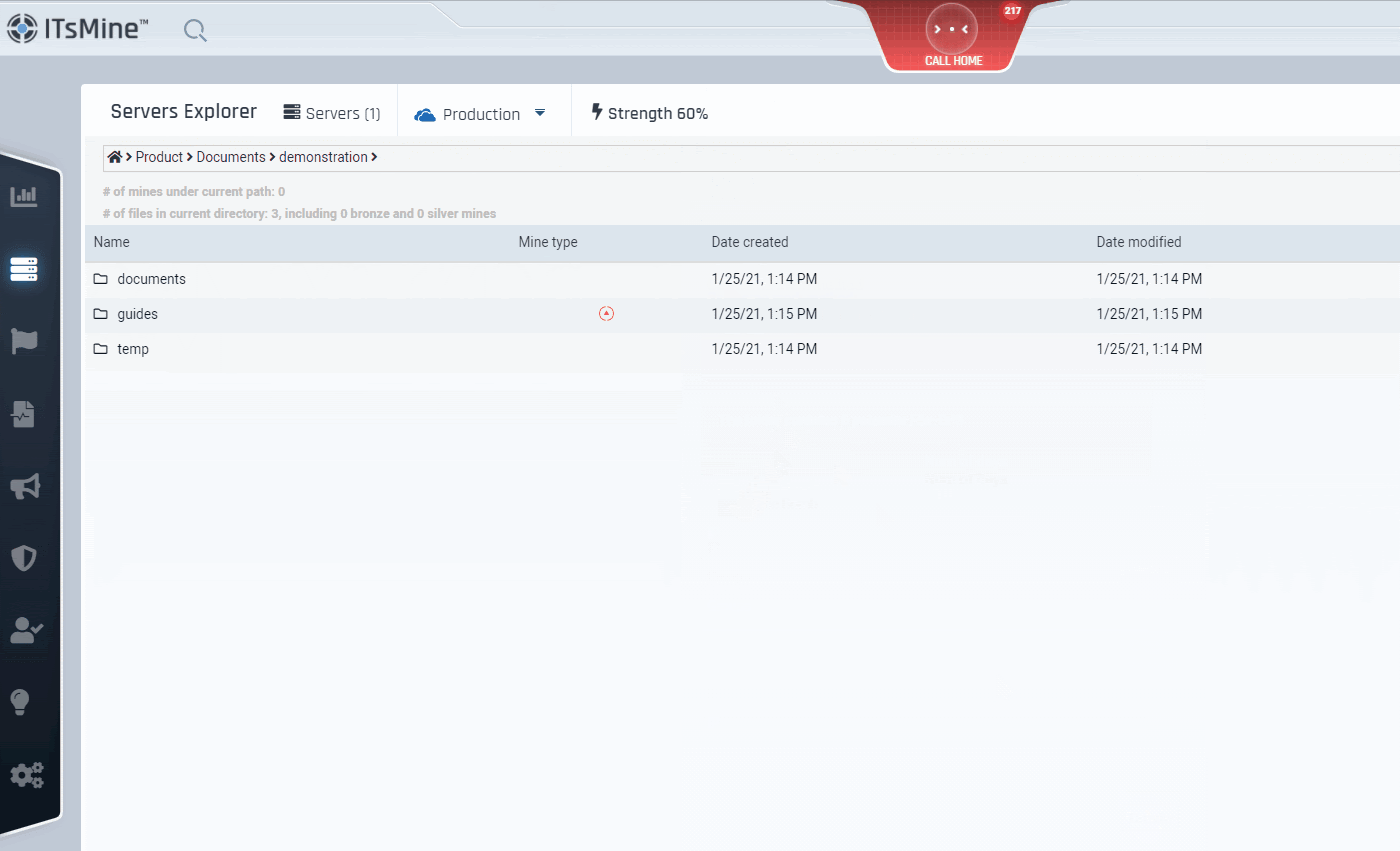
For files from the Vitual Vaults. You can also choose to set expiration dates for data outside your Virtual Vaults, or immediatley kill it. Once the expiration date has been reached, the data outside of the company’s file server will be locked and become unusable, even beyond the company boundaries. The data itself, however, will remain valid and visible within the file server.